GTP stands for the GPRS Tunneling Protocol and is used to encapsulate user data when passing through core network and also carries bearer specific signalling traffic between various network nodes.
Functionality Of GTP
- It provides mobility. When UE is mobile, the IP address remains same and packets are still forwarded since tunneling is provided between PGW and eNB via SGW
- Multiple tunnels (bearers) can be used by same UE to obtain different network QoS
- Main IP remains hidden so it provides security as well
- Creation, deletion and modification of tunnels in case of GTP-C
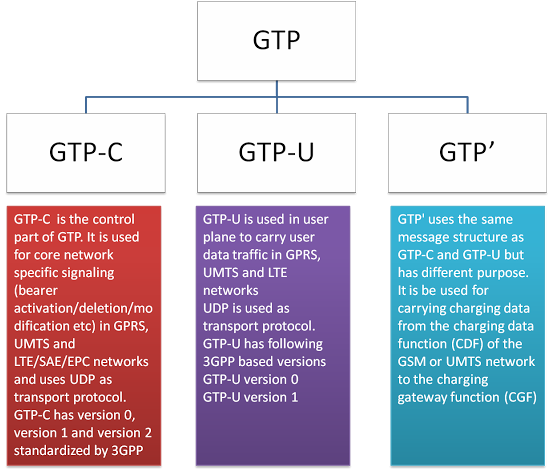
Types of GTP Protocol
Various GTP Interfaces in LTE
GTP-C - Version 2
GTP-U - Version 1
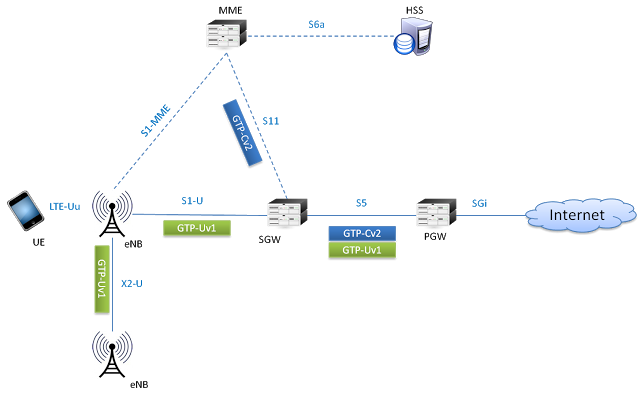
In LTE network GTP-v2 is used on S5 and S11 interfaces and GTPv1 is used on S1-U, S5, X2-U interfaces (as shown below). In inter-RAT and inter PLMN connectivity, S3, S4, S8, S10, S12 and S16 interfaces also utilize GTP protocols
GTP-U
GTP-U encapsulation of UE user plane traffic can be understood by following example. Lets see what happens when IP packet generated by UE reaches to eNodeB and is then forwarded to SGW.
Consider any application on UE creates an IP/TCP packet. This packet consist of actual data by application, TCP or UDP header and then IP field information which has source address of UE and destination address of application server (e.g. Twitter)

When the eNodeB receives this packet over air interface, it will put the IP packet inside GTP header which has information related to tunnel IDs. Then further, it is encapsulated inside UDP and IP header and forwarded as ethernet frame towards SGW. Here the IP header contains eNodeB IP as a source address and SGW IP as a destination address
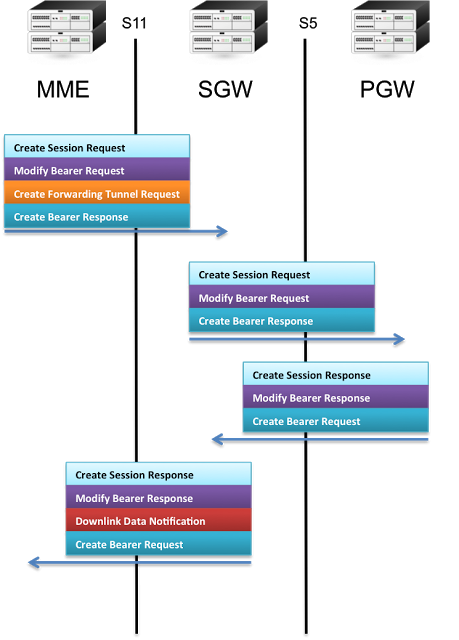
GTP-C
As GTP-Cv2 in LTE is used for tunnel management, some of the signalling messages cab be seen in the following figure -
GTP' (GTP prime)
GTP' uses the same message structure as GTP-C and GTP-U, but has an independent function. It can be used for carrying charging data from the charging data function (CDF) of the LTE network to the charging gateway function (CGF) over a Ga Interface.
