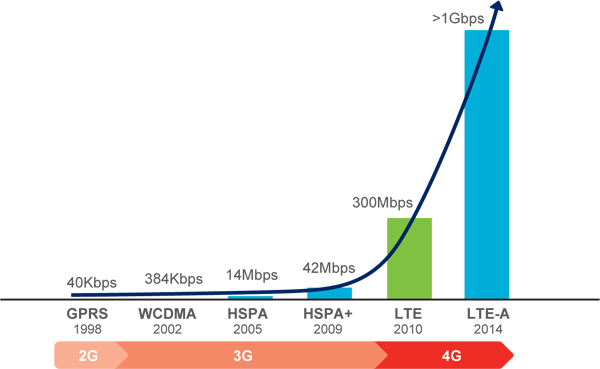
The LTE-based fourth-generation (4G) wireless landscape has become the new nexus where IT industry leaders from device makers to software developers to network operators are pursuing new business opportunities amid consumers demand for faster and more reliable networks. However, the concurrent mention of LTE and LTE Advanced networks in trade media may create a degree of confusion among managers who are not directly associated with LTE network technology.
This article attempts to make a clear distinction between regular LTE and LTE Advanced wireless networks. Long Term Evolution or LTE, as the name suggests, is actually evolution of the existing 3G standard, not a new standard in its own right. In fact, LTE is simply an advanced form of 3G, also called 3.9G by the ITU. However, LTE represents a paradigm shift from hybrid voice and data networks to data-only networks. LTE offers a theoretical capacity of up to 100 Mbit/s in the downlink and 50 Mbit/s in the uplink, and more if a more powerful MIMO technique for antenna arrays is used.
LTE Advanced, like its lower-speed predecessor, is going to be built on the prior LTE OFDM/MIMO architecture to further increase data rate and is being defined in 3GPP Releases 10 and 11. The LTE Advanced standard promises more than three times data speeds than basic LTE networks. It does it by incorporating five high-octane network features: carrier aggregation, increased MIMO, coordinated multipoint transmission, heterogeneous network (HetNet) support, and relays.
LTE Advanced Building Blocks:
First, the carrier aggregation scheme allows mobile operators to utilize more than one 20 MHz bandwidth carrier as specified in the original LTE specification, and in this way, increase the overall transmission capacity. Carrier aggregation technique combines up to five 20-MHz channels into one stream to increase data speed, making possible a peak downlink data rate of 1 Gbit/s.
Second, while the standard LTE defines MIMO configurations of up to 4x4arrangements, LTE Advanced technology extends that to 8x8 stream with support for multiple transmit antennas in the handset. MIMO is a fundamental element of the LTE system design and the first version of the LTE standard supports 2×2 MIMO in both the downlink and uplink. Subsequent developments will extend this capability, and the LTE Advanced systems will eventually support 8×8 MIMO in the downlink and 4×4 MIMO in the uplink.
Third, coordinated multipoint transmission (CoMP)—also known as cooperative MIMO—is a set of techniques that uses different forms of MIMO and beamforming to send and receive radio signals from multiple cells to a mobile device to reduce interference from other cells and ensure optimum performance at the cell edges. SK Telecom, which claims to have launched the world’s first commercial LTE Advanced network in summer 2012, actually used an early stage of coordinated multipoint to allow multiple base stations to communicate with a single device simultaneously.
Fourth, the LTE Advanced standard defines another base station type called relay station. The use of technologies such as MIMO, OFDM, and advanced error correction improves throughput, but they don’t fully mitigate the problems experienced at the cell edge. LTE relays can be used to increase the coverage outside the main area and to fill small holes in coverage.
Finally, heterogeneous network or HetNet is a multi-layered system of overlapping big and small cells which pumped out cheap bandwidth. Several small cells can be distributed within the area covered by a macrocell to provide extra capacity and fill in the gaps in cellular coverage. Mobile phone operators are very excited about moving to HetNets, which incorporate hundreds if not thousands of small cells or low-powered radio access nodes, which in turn, provide nearly the same functionality for a small region as of a larger radio base station.
Inevitably, LTE Advanced will be forward and backward compatible with basic LTE, meaning LTE handsets will work on LTE Advanced networks, and LTE Advanced handsets will work on standard LTE networks. That makes LTE a stepping stone to the much-higher-capacity LTE Advanced systems. The deployment of LTE Advanced networks is expected in 2014 and beyond.


